In today's digital era, securely connect remote IoT P2P SSH Raspberry Pi free has become a crucial topic for tech enthusiasts and professionals alike. As IoT devices continue to grow in popularity, ensuring secure connections is paramount to safeguarding sensitive data and maintaining privacy. This article will explore the methods, tools, and best practices to achieve secure remote connections using SSH on a Raspberry Pi.
With the increasing reliance on interconnected devices, the need for secure communication channels has never been more critical. Whether you're a hobbyist setting up a home automation system or a professional managing an extensive IoT network, understanding how to establish secure connections is essential.
This guide will provide you with step-by-step instructions, expert insights, and actionable tips to help you connect your Raspberry Pi securely and efficiently. By the end of this article, you'll have a comprehensive understanding of how to leverage SSH for remote IoT connectivity without compromising security.
Table of Contents
- Introduction to SSH
- Raspberry Pi Overview
- Setting Up SSH on Raspberry Pi
- Secure Remote Connections
- IoT P2P Connections
- Best Practices for Security
- Troubleshooting Common Issues
- Frequently Asked Questions
- References
- Conclusion
Introduction to SSH
SSH, or Secure Shell, is a network protocol designed to provide secure communication between two devices over an unsecured network. It encrypts all data transmitted between the client and server, ensuring that sensitive information remains private and protected from unauthorized access.
For those looking to securely connect remote IoT P2P SSH Raspberry Pi free, SSH is an ideal solution. It not only secures data transmission but also provides authentication mechanisms to ensure that only authorized users can access the system.
SSH operates on port 22 by default and supports various encryption algorithms, such as AES, Blowfish, and Triple DES. These features make it a robust tool for managing remote devices, including Raspberry Pi-based IoT setups.
Raspberry Pi Overview
The Raspberry Pi is a compact, affordable, and versatile single-board computer that has revolutionized the world of DIY electronics and IoT projects. Its small form factor, low power consumption, and extensive community support make it an ideal platform for experimenting with IoT applications.
With its built-in GPIO pins and support for various operating systems, the Raspberry Pi can be configured to act as a server, client, or gateway in an IoT network. By leveraging SSH, users can remotely manage their Raspberry Pi devices, enabling seamless integration into larger IoT ecosystems.
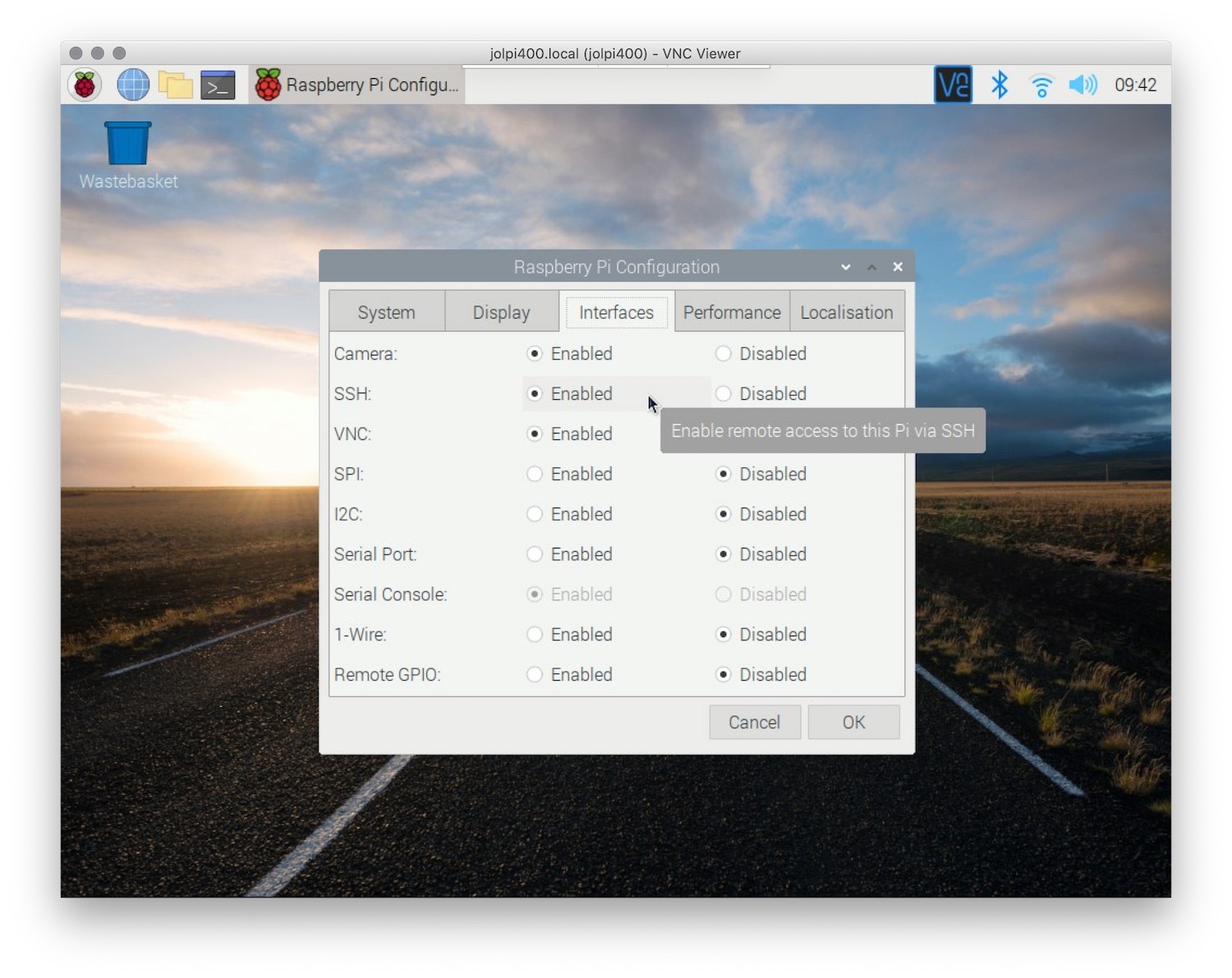
Setting Up SSH on Raspberry Pi
Configuring SSH on a Raspberry Pi is a straightforward process that can be accomplished in just a few steps. Below is a detailed guide to help you set up SSH on your Raspberry Pi:
- Enable SSH on your Raspberry Pi by navigating to the Raspberry Pi Configuration menu and selecting the SSH option.
- Alternatively, you can enable SSH by creating an empty file named "ssh" in the boot partition of your SD card.
- Once SSH is enabled, note the IP address of your Raspberry Pi, which can be obtained by running the command
ifconfigorip addr. - From your remote device, use an SSH client such as PuTTY (for Windows) or the built-in terminal (for macOS and Linux) to connect to your Raspberry Pi using the command
ssh pi@.
Secure Remote Connections
Firewall Configuration
Configuring a firewall is an essential step in securing your Raspberry Pi's SSH connection. By limiting access to only trusted IP addresses, you can significantly reduce the risk of unauthorized access.
Use tools like ufw (Uncomplicated Firewall) to set up basic firewall rules. For example, you can allow SSH traffic on port 22 by running the command sudo ufw allow 22. Additionally, consider changing the default SSH port to a non-standard port to further enhance security.
Encryption Methods
SSH employs several encryption methods to secure data transmission. Understanding these methods can help you choose the most appropriate one for your specific use case.
Some of the commonly used encryption algorithms in SSH include:
- AES (Advanced Encryption Standard)
- Blowfish
- Triple DES
By default, SSH uses AES as its encryption algorithm, but you can modify this setting in the SSH configuration file (/etc/ssh/sshd_config) if needed.
IoT P2P Connections
In the context of IoT, P2P (Peer-to-Peer) connections allow devices to communicate directly with each other without the need for a central server. This approach can reduce latency and improve overall system performance.
When securely connecting remote IoT P2P SSH Raspberry Pi free, it's important to consider the following:
- Ensure that all devices in the network are authenticated and authorized to communicate with each other.
- Implement encryption protocols to protect data transmitted between devices.
- Regularly update firmware and software to address potential security vulnerabilities.
Best Practices for Security
To ensure the highest level of security when securely connecting remote IoT P2P SSH Raspberry Pi free, follow these best practices:
- Use strong, unique passwords for all user accounts.
- Enable two-factor authentication (2FA) whenever possible.
- Regularly monitor system logs for suspicious activity.
- Keep your operating system and software up to date with the latest security patches.
Troubleshooting Common Issues
Despite following best practices, you may encounter issues when setting up SSH on your Raspberry Pi. Below are some common problems and their solutions:
- Connection Refused: Ensure that SSH is enabled and the correct IP address is being used.
- Authentication Failed: Verify that the correct username and password are being entered.
- Timeout Errors: Check your network connection and ensure that the firewall is not blocking SSH traffic.
Frequently Asked Questions
Here are some frequently asked questions related to securely connecting remote IoT P2P SSH Raspberry Pi free:
- Q: Can I use SSH on other operating systems besides Raspberry Pi?
- A: Yes, SSH can be used on various operating systems, including Linux, macOS, and Windows.
- Q: Is SSH the only way to secure IoT connections?
- A: While SSH is a popular choice, there are other protocols like TLS and DTLS that can also be used for securing IoT connections.
References
This article draws on information from the following sources:
Conclusion
In conclusion, securely connecting remote IoT P2P SSH Raspberry Pi free is a critical aspect of modern IoT deployments. By following the steps and best practices outlined in this guide, you can ensure that your Raspberry Pi-based IoT network remains secure and efficient.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT, cybersecurity, and Raspberry Pi projects.